Configuring Secrets and Environment Variables
Overview
Now that the foundational setup is complete, this guide will walk you through configuring secrets and environment variables within both GitHub and Terraform Cloud.
Terraform Cloud Configuration
-
Log in to Terraform Cloud and select the DSB organization.
-
On the left-hand menu, click Settings > Variable Sets. You should see a screen similar to this:
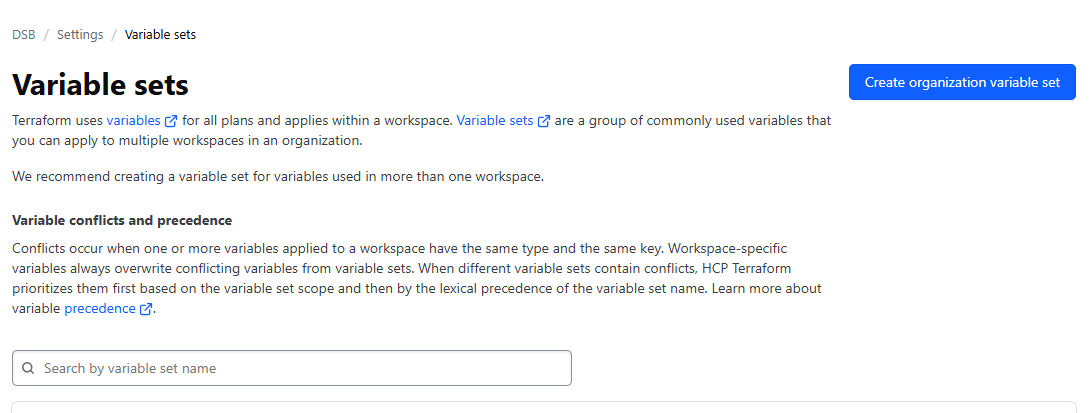
-
Click Create Organization Variable Set, and fill in the following details:
- Name: Provide a meaningful name for the variable set.
- Description: Add a brief description for clarity.
- Variable Set Scope: Select Apply to all projects and workspaces. (You can modify this later if needed.)
-
Scroll down to the Variables section and click Add Variable. Add the following keys, marking them as Environment Variables:
TFC_AWS_PROVIDER_AUTH: Set this totrue.TFC_AWS_RUN_ROLE_ARN: Paste the Role ARN that you saved earlier here.
-
After adding the variables, your variable set should look similar to this:
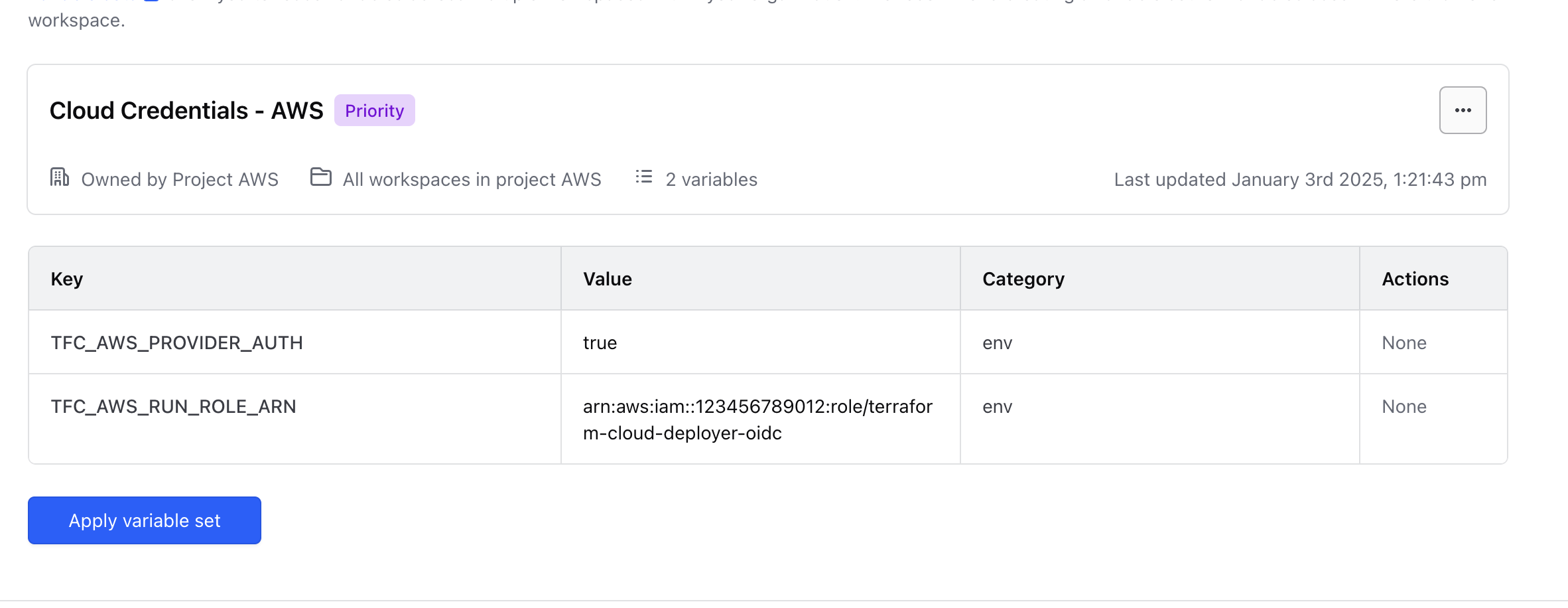
GitHub Configuration
After forking the repositories, you need to configure the necessary secrets for GitHub Actions in the aws-devsecops-pipeline repository. These secrets will enable automated deployments when updates are pushed to the main branch.
- Log in to GitHub and open the
aws-devsecops-pipelinerepository. - Navigate to Settings > Secrets and Variables under the Security section.
- Click Actions, then select New Repository Secret.
- Create a secret with the name
TF_API_TOKENand paste the Terraform Cloud token you generated earlier.
With these steps completed, your repositories and environment are fully configured and ready for use.